Weerarada Cyber - Qeexid, Noocyada, Ka Hortagga
Weerar Cyber(Cyber Attack) - ku waa weerar laga soo bilaabo kombuyuutar ka dhan ah kombuyuutar kale ama degel kale, iyada oo ujeedadu tahay in la waxyeeleeyo daacadnimada, sirta ama helitaanka bartilmaameedka iyo macluumaadka ku kaydsan. Maqaalkani wuxuu sharxayaa waxa ay yihiin weerarrada internetka(Cyber Attacks) , qeexitaankeeda, noocyada iyo ka hadalka sida looga hortago iyo koorsada la qaato haddii ay dhacdo weerar internet. Weerarada internetka(Cyber Attacks) , sinaba, waxaa si balaadhan loogu tixgalin karaa inay qayb ka tahay dambiyada internetka(Cyber Crime) . Weerar lagu galo Dembiyada Internetka(Cyber Crime) waxa loogu yeedhi karaa Weerar Cyber!
Qeexida Weerarada Internetka
Sida laga soo xigtay Shirkadda Sharciga ee Practical Law(Practical Law Company) , warqad cad(Whitepaper) oo ku saabsan weerarrada internetka(Cyber Attacks) , oo ay maamusho hklaw.com , qeexida weerarrada internetka(Cyber Attacks) waa sida soo socota:
A Cyber Attack is an attack initiated from a computer against a website, computer system or individual computer (collectively, a computer) that compromises the confidentiality, integrity or availability of the computer or information stored on it.
Qeexitaanku waxa uu leeyahay saddex arrimood oo kala duwan: [1 ] Weerar(] Attack) ama isku day sharci darro ah oo lagu [2] wax lagaga helayo nidaamka kombiyuutarka [3]. Guud ahaan, nidaamku waa ururin unugyo ah oo si wadajir ah uga shaqeeya ujeedo guud. Sidaa darteed, haddii ay tahay hal ama kombuyuutar ururin ah - offline ama online (website / intranet), waa nidaam marka ay u shaqeeyaan si ay u fududeeyaan shay ama mid kale. Xataa kombuyuutarku waxa uu leeyahay qaybo badan oo ka wada shaqeeya hadaf midaysan oo markaa waxa loo yaqaan nidaamka kombayutarka.
Qodobka ugu muhiimsan waa gelitaanka sharci-darrada(illegal access) ah ee nidaamkan. Qodobka labaad waa habka bartilmaameedka(target system) . Qodobka ugu dambeeya waa guulaha laga gaaro weerarka(attacker) . Waa in la ogaadaa in gelitaanka sharci-darrada ah ay tahay in ay leedahay ujeedo lagu carqaladeynayo nidaamka bartilmaameedka, si uu u helo wax weerar ah, sida macluumaadka ku kaydsan nidaamka, ama guud ahaan xakamaynta nidaamka.
Akhri: (Read:) Waa maxay sababta loo jabsado mareegaha ?
Noocyada Weerarada Internetka
Waxaa jira habab badan oo weerarrada internetka(Cyber Attacks) laga bilaabo duritaanka malware ilaa phishing ilaa injineernimada bulshada ilaa xatooyada gudaha ee xogta. Foomamka kale ee horumarsan laakiin kuwa caadiga ah waa Weerarrada DDoS(DDoS Attacks) , Weerarrada Ciidanka Brute(Brute Force attacks) , jabsiga, haynta nidaamka kombiyuutarka (ama degel) madax furasho iyadoo la adeegsanayo jabsiga tooska ah ama Ransomware .
Qaar ka mid ah iyaga ayaa hoos lagu taxay:
- Helitaanka, ama isku dayga in lagu kasbado, galitaanka aan la ogolayn ee nidaamka kombiyuutarka ama xogtiisa.
- Burburinta ama diidmada weerarrada adeegga ( DDoS )
- Jabsiga website ama si xun u wajahdo goobta
- Ku rakibida fayraska ama malware
- Isticmaalka kumbuyuutarka ee aan la ogolayn ee habaynta xogta
- Isticmaalka aan habboonayn(Inappropriate) ee kombuyuutarrada ama codsiyada ay adeegsadaan shaqaalaha shirkaddu, si ay waxyeello ugu geystaan shirkadda.
Midda ugu dambeysa - isticmaalka aan habboonayn ee kombuyuutarrada ama apps-ka ee shaqaaluhu - waxay noqon kartaa ula kac ama aqoon la'aan awgeed. Waa in la ogaadaa sababta dhabta ah ee qofka shaqaalaha ah, tusaale ahaan, uu isku dayay in uu galo xog khaldan ama uu galo xog gaar ah oo aan loo ogolayn in uu beddelo.
Injineernimada bulshadu(Social engineering) waxay sidoo kale noqon kartaa sabab uu shaqaaluhu si ula kac ah isugu dayo inuu jabsado xogta - kaliya si uu u caawiyo saaxiib! Taasi waa, shaqaaluhu wuxuu saaxiib la ahaa dambiile waxaana lagu qasbay niyadda inuu helo xog aan waxba galabsan saaxiibka cusub.
Inta aan halkan joogno, waxaa sidoo kale habboon in la baro shaqaalaha khatarta WiFi-ga dadweynaha(dangers of public WiFi) iyo sababta aysan u isticmaalin WiFi-ga dadweynaha ee shaqada xafiiska.(While we are here, it is also advisable to teach the employees about the dangers of public WiFi and why they should not use public WiFi for office work.)
Akhri(Read) : Maxay yihiin Honeypots iyo sida ay u sugi karaan nidaamyada kombiyuutarka.
Jawaabta Weerarada Internetka
Ka-hortagga had iyo jeer way ka fiican tahay daawaynta. Waa in aad tan maqashay dhowr jeer. Isla sidaas oo kale ayaa khuseeysa goobta IT-ga marka ay timaaddo ka hortagga weerarrada internetka(Cyber Attacks) . Si kastaba ha ahaatee, iyada oo loo malaynayo in kombuyuutarkaaga ama mareegahaaga (yada) la weeraray, xitaa ka dib markii la qaaday dhammaan taxaddarrada, waxaa jira tallaabooyin jawaab celin guud oo gaar ah oo la dejiyay:
- Weerarku run ahaantii ma(Did) dhacay mise qof baa soo wacaya si uu u ciyaaro;
- Haddii aad weli marin u leedahay xogtaada, dib u celi;
- Haddii aadan heli karin xogtaada, oo uu jabsadayhu uu dalbanayo madaxfurasho, waxaa laga yaabaa inaad rabto inaad tixgeliso inaad la xiriirto hay'adaha sharciga
- Kala xaajoonta jabsiga oo dib u soo cesha xogta
- Marka laga hadlayo injineernimada bulshada iyo shaqaaluhu si khaldan u isticmaalayaan xuquuqdooda, hubinta waa in la sameeyaa si loo go'aamiyo haddii shaqaaluhu aanu dambi lahayn ama uu u dhaqmay si ula kac ah.
- Marka laga hadlayo weerarrada DDoS , culeyska waa in la dhimo server-yada kale, si uu mareegta ugu soo laabto khadka sida ugu dhaqsaha badan. Waxa laga yaabaa inaad kiraysato server-yada in muddo ah ama aad isticmaasho abka daruuraha si kharashyadu u yaraado.
Si aad u hesho macluumaad sax ah oo faahfaahsan oo ku saabsan ka jawaabista dariiqa sharciga ah, fadlan akhri warqadda cad ee lagu sheegay qaybta Tixraaca(References) .
Akhri(Read) : Muxuu qof u doonayaa inuu jabsado kombayutarkayga?(Why would someone want to hack my computer?)
Kahortagga Weerarada Internetka
Waxa laga yaabaa inaad horeba u ogaatay in aanu jirin 100% hab nacasnimo ah oo lagaga hortagayo dambiyada internetka iyo weerarada interneedka, laakiin haddana, waa inaad samaysaa taxadar badan si aad u ilaaliso kombayutaradaada.
Waxyaabaha ugu horreeya ee la sameeyo waa in la isticmaalo software wanaagsan oo amniga ah, kaas oo aan kaliya iska baari karin fayraska, laakiin sidoo kale wuxuu raadiyaa noocyo kala duwan oo malware ah, oo ay ku jiraan laakiin aan ku xaddidneyn ransomware, oo joojiya inuu galo kombiyuutarka. Inta badan(Mostly) code-yadan xaasidnimada leh waxaa lagu duraa kombuyuutarkaaga adigoo booqanaya ama ka soo dejisanaya waxyaabaha mareegaha aan sumcadda lahayn, Drive-by downloads , shabakadaha khatarta ah ee muujiya xayaysiisyada xunxun sidoo kale loo yaqaan Malvertising .
Iyada oo ay la socoto antivirus-ka, waa inaad isticmaashaa dab-damis wanaagsan. In kasta oo uu ku dhex dhisan yahay dab-damiska gudaha Windows 10/8/7 uu fiican yahay, waxaad isticmaali kartaa dab-damisyada qolo saddexaad oo aad dareento inay ka xoog badan yihiin kan caadiga ah ee Firewall Windows(Windows Firewall) .
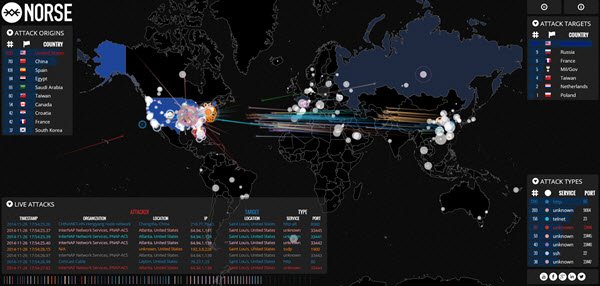
Akhri(Read) : Khariidadaha Tracker-ka Malware kaas oo kuu ogolaanaya inaad aragto Weerarada Cyber(Cyber Attacks) waqtiga dhabta ah.
Haddii ay tahay shabakad kombuyuutar shirkadeed, hubi in aysan jirin taageero Plug and Play mid ka mid ah kombiyuutarada isticmaala. Taasi waa, shaqaaluhu waa inaysan awoodin inay ku xidhaan darawallada Flash ama dongleskooda internetka(Internet) gudaha USB-ga(USB) . Waaxda IT ee shirkadu waa inay sidoo kale ilaaliso dhammaan taraafikada shabakada. Isticmaalka falanqeeye taraafikada shabakad wanaagsan waxay caawisaa ka qaybgalka degdega ah ee dabeecadaha qariibka ah ee ka soo baxa terminal kasta (kumbuyuutar shaqaale).
Akhriso(Read) : Hababka Badbaadada Internetka ee ugu Wanaagsan ee Ganacsiga Yaryar(Best Cybersecurity Practices for Small Business) .
Si loo ilaaliyo weerarrada DDoS , degelka si fiican ayaa loo yareeyaa adeegayaal kala duwan, halkii si fudud loogu martigelin lahaa hal server. Habka ugu fiican wuxuu noqon lahaa in muraayad si joogto ah kor loogu qaado iyadoo la isticmaalayo adeegga daruuriga. Taasi waxay aad u yaraynaysaa fursadaha DDoS ku guulaysanayso -ma aha wakhti dheer ugu yaraan. Isticmaal dab-damis wanaagsan sida Sucuri oo qaado tillaabooyin aasaasi ah si aad u ilaaliso oo aad u sugo mareegahaaga.
Waa kuwan dhowr xiriiriye oo faa'iido leh oo muujinaya khariidadaha weerarka jabsiga dhijitaalka ah ee waqtiga-dhabta ah:(Here are a few useful links that display real-time digital hack attack maps:)
- ipviking.com
- digitalattackmap.com
- fireeye.com
- norsecorp.com
- honeynet.org.
Bal u fiirso iyaga. Waxay yihiin kuwo aad u xiiso badan!
Haddii aad hayso wax aad ku darto, fadlan la wadaag.(If you have anything to add, please do share.)
Akhri marka xigta(Read next) : Weerarrada lagu buufiyo Password-ka(Password Spray Attacks) | Weerarada Xoogan(Brute Force Attacks) | Ku noolaanshaha Weerarkii Dhulka(Living Off The Land attacks) | Weerarada Doomaha(Surfing Attacks) | Weerarada Walaxda Aqoonsiga | Domain Fronting | Weerarada kabaha qabow(Cold Boot Attacks) .
Related posts
Waa maxay dambiyada internetka? Sidee wax looga qabtaa?
Qaababka Madow: Khiyaamooyinka Mareegta, Tusaalooyinka, Noocyada, Sida Loo Arko & Iska Ilaali
Sida loo hubiyo in xiriirku uu badbaado yahay ama aan la isticmaalin biraawsarkaaga
Soo ogow in akoonkaaga onlaynka ah la jabsaday & iimaylka & faahfaahinta sirta ah oo la daatay
Talooyin Badbaadada onlaynka ah ee Carruurta, Ardayda iyo Dhallinyarada
Soo-gudbinta Malware: Halkee loo gudbiyaa faylasha malware-ka Microsoft iyo kuwa kale?
Farta browserka. Sida loo damiyo Sawirada Faraha ee browserka
Sida loo isticmaalo browserka Chrome ka ee la dhisay Malware Scanner & Qalabka Nadiifinta
Weerarada Malware-ka aan fileyn, Ilaalinta iyo Ogaanshaha
Sida loo isticmaalo Avast Boot Scan si looga saaro Malware-ka Windows PC
Waa maxay Fleeceware? Sidee iskaga ilaalin kartaa abka Fleeceware?
Dib u eegista browserka VPN ee bilaashka ah ee Globus: Siri dhammaan taraafikada, baadh si qarsoodi ah
Taxaddar la qaado ka hor intaanad gujin xiriiriyeyaasha shabakadda ama URL-yada
Waa maxay Weerarka Dhexe ee Man-In-The-Middle (MITM): Qeexid, Ka-hortagga, Qalabka
Weerarada Nuglaanta Afduubka DLL, Kahortagga & Ogaanshaha
Barnaamijyada ama Codsiyada aan la rabin ee suurtogalka ah; Iska ilaali inaad ku rakibto PUP/PUA
Waa maxay khiyaanada Whaling & sida loo ilaaliyo ganacsigaaga
Soosaaraha Magaca beenta ah ee bilaashka ah si loo dhaliyo Aqoonsi Been abuur ah
Khatarta iyo Cawaaqib xumada ka dhalan karta wadaagga badan ee Baraha Bulshada
Ka saar fayraska USB Flash Drive adoo isticmaalaya Command Prompt ama Faylka Dufcada
